- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Stay ahead of threats with new innovations from Azure Sentinel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Azure Sentinel became generally available almost exactly a year ago in the weeks leading up to Microsoft Ignite 2019. The world has changed pretty dramatically since then, but our dedicated team of security researchers and engineers have kept focus on their goal of empowering defenders to combat rapidly evolving threats with increased efficiency.
With COVID19 driving cloud adoption and remote work, security operations teams are tasked with securing an increasingly distributed estate, and with budgets tightening due to macroeconomic concerns, managing costs has become even more imperative.
So, while this Microsoft Ignite 2020 will be a bit different, and I will miss connecting with many of you in person, I think you will find that our mission has remained steadfast and the lineup of new features launching this year will be as impactful as ever.
UEBA + Entity Profiles:
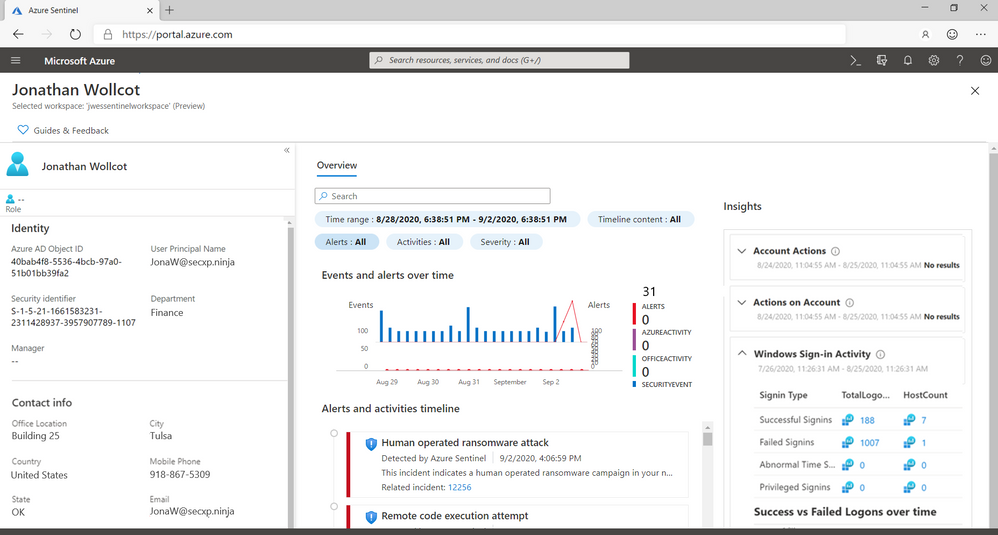
Azure Sentinel is launching User and Entity Behavioral Analytics, powered by Microsoft’s proven UEBA platform, to help detect unknown and insider threats. It works by building a comprehensive profile across time and peer groups horizons to identify anomalous activities and add behavioral insights for threat hunting and detection. Unlike other UEBA solutions, onboarding data sources for behavioral analysis takes just minutes. A UEBA workbook provides an interactive dashboard for investigating suspect users, and built-in queries and analytic rules leverage behavioral insights and anomalies for threat hunting and detection.
New entity profiles provide a unified view of a user or host, including insights from UEBA, with additional entity types coming soon. Analysts can perform a simple text search (by entity name or another identifier) to find and open an entity profile, or by clicking on an entity while hunting or investigating an incident. The profile includes contextual information, a timeline of activities and alerts across the most relevant data sources, and insights to inform decision making.
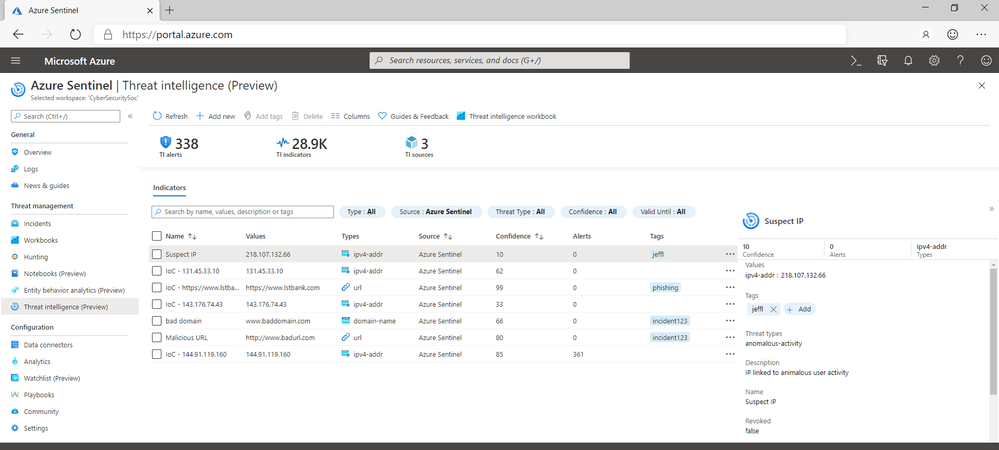
Threat Intelligence
The ability to monitor and respond to changing threats is critical to the success of any security operations team. Tracking and applying intelligence from multiple sources is much easier with the introduction of a new threat intelligence experience in Azure Sentinel. From the new blade, security analysts can view, filter, tag and search indicators imported from threat intelligence providers as well add new indictors discovered while hunting and investigating threats in Azure Sentinel. As before, indicators can be automatically matched against your security data to find threats targeting your organization and provide insights into the prevalence and source of attacks, which can be used to prioritize your response.
In addition to support for data collection via TAXII, new integration and automation options enable customers to import threat intelligence from additional sources and automate enrichment of security incidents. These include:
- Recorded Future has developed a connector for Azure Logic Apps and playbooks to automate importing indicators and enriching incidents in Azure Sentinel with data from its security intelligence platform. Similarly, an Azure Logic Apps connector and playbooks from RiskIQ enables customers to automatically enrich incidents in Azure Sentinel with data from the RiskIQ Internet Intelligence Graph. Similarly,
- ThreatConnect, ThreatQuotient, EclecticIQ have joined the list of leading third-party providers that can send indicator feeds directly to Azure Sentinel using the built-in Threat Intelligence Platforms connector.
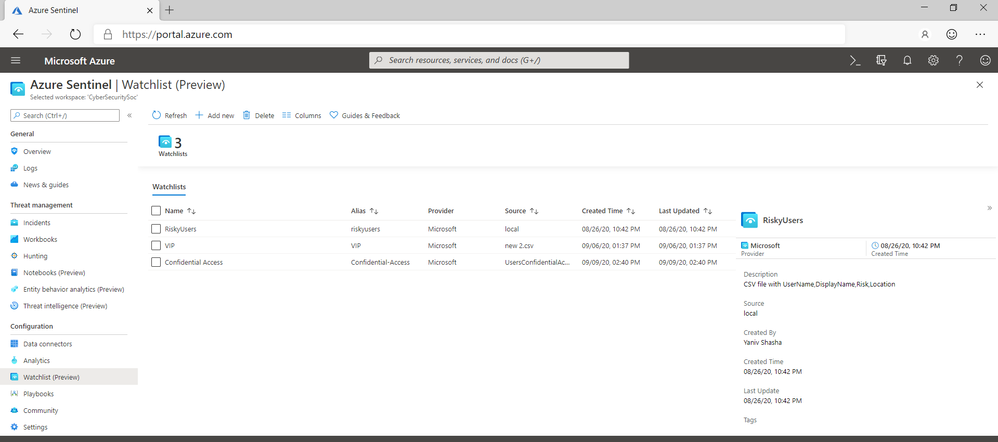
Watchlists
Analysts often need the ability to correlate security events and insights with other non-security data sources, such as lists of critical assets, trusted systems, or terminated employees. This is often done through time consuming, manual analysis of external data sources. Within the next few weeks, customers will be able to easily import collections of data from external sources as a watchlist in Azure Sentinel. Watchlists can then be used in analytics rules, threat hunting, workbooks, notebooks and within any query as allow/deny lists, contextual clues, and more. Watchlists currently supports CSV file uploads with more options and updates coming soon.
Enterprise-Wide Data Collection
To simplify the process of collecting data at scale from you users, decides, apps, and infra, both on-premises and in the cloud, Azure Sentinel is continuing to deliver new connectors for Microsoft 365 and Azure, as well as other clouds and data collection pipelines. Here are the latest additions:
- Microsoft 365: The Office 365 connector has been extended to support Microsoft Teams activity logs in addition to SharePoint and Exchange. We’ve released an integration. And, in the coming weeks a connector will add support for raw log data from Microsoft Defender for Endpoint.
- Azure: Additional visibility into Azure networking data is available through new connectors for Azure Firewall, Azure WAF, and Azure DDoS.
- Security Products: A growing ecosystem of data connectors powers integration with third party services. In addition to the dozen plus connectors released this Summer, connectors are now available for CyberArk, Citrix WAF (formerly NetScaler WAF), ForgeRock, and Beyond Security.
- Logstash: A new plug-in enables you to use Azure Sentinel as the output for Logstash, an open source data processing pipeline.
In addition, a new schema, based on the Open Source Security Events Metadata ( ) project, provides a common information model for networking data as well as guidelines for normalizing various entities Customers can write parsers to align networking data from disparate sources for easier analysis and correlation.
Machine Learning
Azure Sentinel makes extensive use of machine learning to fuel built-in analytics, developed by Microsoft security experts and informed by decades of protecting Microsoft services at massive scale. We are continuously developing and refining machine learning models to extend coverage across the MITRE ATT&CK kill chain and address evolving threats. At Microsoft Ignite, we are adding that leverage machine learning to fuse together alerts and events from multiple sources into high severity incidents.
In addition, we are enabling security analysts and data scientists to leverage machine learning to power custom threat hunting and detections in two new ways:
- Notebooks + Azure Machine Learning: Notebooks in Azure Sentinel are now running on the Azure Machine Learning service, providing a highly customizable Jupyter notebook experience for analyzing your security data, all within a secure Azure cloud environment. Azure Machine Learning offers Intellisense for improved ease of use, support for existing Jupyter and JupyterLab experiences, as well as point-in-time notebook snapshots and a notebook file explorer for easy notebook collaboration. Dedicated compute and multiple pricing options provide increased flexibility and control. Take advantage of built-in security analytics via MSTICPy and Jupyter notebook templates help you get started.
- Build-Your-Own Machine Learning: A new machine learning framework, including data pipelines, tools, and templates, helps you accelerate development of ML models for your unique use cases, leveraging Microsoft’s shared ML algorithms and best practices. Integration with familiar development environments, tools, and programming languages, like Azure Databricks, Spark, Jupyter Notebooks and Python, reduces the learning curve and development time. The framework makes use of new auto-export capabilities to stream data from your Azure Sentinel workspace to Blob storage or an Event Hub for use in Azure Databricks. You can then use the notebooks included in the ML package to start building your models, score the results and write them back to Azure Sentinel.
IoT/OT
The recent Microsoft acquisition of CyberX opens up exciting new opportunities for organizations to gain security insights into OT networks and devices. Insights from CyberX will be integrated with Azure Defender for IoT and available in October through the existing data connector in Azure Sentinel. This will enable security analysts to detect and defend against attacks that span IT and IoT/OT networks. In addition, sample automation playbooks enable swift action to triage and remediate threats targeting OT environments from within Azure Sentinel.
Community
The Azure Sentinel Threat Hunters community on GitHub continues to grow with over 650 contributions - see the leaderboard for a list of top contributors. The Azure Sentinel Hackathon concluded recently with some awesome cybersecurity solutions. Check out the winning app at Microsoft Ignite 2020 Architecting SecOps for Success session.
Get Started and Save Costs
With tightening budgets, security operations teams need cost savings and efficiency more than ever. We are launching two new promotions to help accelerate your migration to cloud while reducing overall IT costs.
- To help accelerate deployment of Azure Sentinel and offset the costs of migrating from an existing SIEM solution, for a limited time eligible customers can get $25,000 in Azure credits when you ingest an average of 50GB/day into Azure Sentinel for three consecutive months. Learn more.
- Additionally, to help Microsoft 365 E5 customers modernize faster, we are offering promotional pricing that will save the typical 3,500 seat deployment $1,500 per month beginning in November . Stay tuned for additional details.
You can access the new features in Azure Sentinel today. If you are not using Azure Sentinel, we welcome you to start a trial.
You can also learn more about the latest innovations by watching these Microsoft Ignite sessions:
- Improve SecOps with Azure Sentinel, your Cloud-Native SIEM - September 22, 2:30 PM PT; September 22, 11:15 PM PT; or September 23, 6:30 AM PT
- Ask the Experts - September 22, 3:15 PM PT; September 23, 3:30 AM PT
- Detect Unknown Threats with User and Entity Behavioral Analytics in Azure Sentinel – On-demand
- Architecting SecOps for Success Best Practices for Deploying Azure Sentinel – Part 1 On-Demand, Part 2 On-Demand
- Use Threat Intelligence to Detect Malicious Activity in Azure Sentinel – On-Demand
- Protecting your remote workforce: Threat hunting in your remote productivity tools with Azure Sentinel – On-Demand
- Detecting and Responding to Threats using Azure Network Security tools and Azure Sentinel – On-Demand
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.