Different Types of Hackers: The 6 Hats Explained
Black hat, white hat, grey hat, red hat, blue hat, and green hat. No, these aren’t items in an apparel store’s catalog — they’re the different types of hackers you’ll find in the cybersecurity industry
The term “hacker” is often portrayed negatively by the media and as being synonymous with cybercriminals. When people hear the word “hacker,” they instantly imagine a shady guy wearing a dark hoodie who works on a computer in a dark basement. Although that description is true for some types of hackers, it’s not applicable to all of them. That’s because there are six different types of hackers in the cybersecurity industry — all of whom have different motives and objectives.
In this article, we’ll explore the six different types of hackers, why they do what they do, and how their activities differ.
What Are the Six Different Types of Hackers?
When it comes to cybersecurity, things aren’t all that black and white (excuse the pun). Hackers’ hats come in a variety of colors:
- White hat
- Grey hat
- Black hat
- Blue hat
- Green hat
- Red hat
So, what are the differences between these different types of hackers? Let’s check it out.
1) Black Hat Hacker
Black hat hackers are the evil guys who want to use their technical skills to defraud and blackmail others. They usually have the expertise and knowledge to break into computer networks without the owners’ permission, exploit security vulnerabilities, and bypass security protocols. To make money, they are ready to do all illegal activities such as:
- Sending phishing emails and SMS messages.
- Writing, distributing, and selling malware like viruses, worms, trojan horses, etc.
- Deploying cyber attacks like distributed denial of service (DDoS) to slow down or crash the websites.
- Earning money for doing political and corporate espionage.
- Finding and exploiting leaky databases and software vulnerabilities.
- Selling financial and personally identifiable information on the Dark Web.
- Executing financial fraud and identity theft-related crimes.
- Deploying dangerous cyber threats like brute-force attacks, scareware, botnets, man-in-the-middle attacks, malvertizing campaigns, etc.
- Blackmailing the victims using ransomware and spyware to encrypt, lock, steal, modify, and delete your data. Black hat hackers typically demand extortion money to give back access to the files, system, databases, or the entire device. They also blackmail victims, threatening to reveal their confidential data, business documents, personal photos, videos, etc., to the public if they don’t pay.
2) White Hat Hacker
When it comes to understanding the different types of hackers, there can’t be a bigger difference than the gulf that exists between white and black hat hackers. White hat hackers (also known as ethical hackers) are the polar opposite of their black hat counterparts. They use their technical skills to protect the world from bad hackers.
Companies and government agencies hire white hats as information security analysts, cybersecurity researchers, security specialists, penetration testers, etc. They work as independent consultants or freelancers as well. White hat hackers employ the same hacking techniques as black hat hackers, but they do it with the system owner’s permission and their intentions are noble.
But what are their motivations? White hat hackers hack to:
- Find and fix vulnerabilities in the system before black hat hackers exploit them.
- Develop tools that can detect cyberattacks and mitigate or block them.
- Strengthen the overall security posture of the software and hardware components.
- Build security software like antivirus, anti-malware, anti-spyware, honeypots, firewalls, etc.
White hat hackers are often academics and researchers who want to better understand various cyber threats and educate others about them. Companies and governments hire them as consultants and practitioners to prepare contingency plans to get ready for cyber attacks and other worst-case scenarios. White hat hackers also help companies adhere to the security guidelines outlined in security and privacy-focused regulations like HIPAA, PCI DSS, GDPR, etc.
Unlike other types of hackers, white hat hackers ensure their activities fall within the legal framework. And this point makes them different from red hat hackers, which we’ll talk about later in the article.
3) Grey Hat Hacker
Next on our list of the different types of hackers is grey hats. These hackers fall somewhere between white hat and black hat hackers. Grey hat hackers’ intentions are often good, but they don’t always take the ethical route with their hacking technics. For example, they may penetrate your website, application, or IT systems to look for vulnerabilities without your consent. But they typically don’t try to cause any harm.
Grey hat hackers draw the owner’s attention to the existing vulnerabilities. They often launch the same type of cyber-attacks as white hats on a company/government servers and websites. These attacks expose the security loopholes but don’t cause any damage. However, again, they do this without the owner’s knowledge or permission. Grey hat hackers sometimes charge a fee to:
- Fix bugs or vulnerabilities,
- Strengthen the organization’s security defenses, or
- Provide recommendations, solutions, or tools to patch vulnerabilities.
Some grey hat hackers release information about vulnerabilities in the public once they are patched. But in many cases, they reach out to the affected companies first to let them know about the vulnerabilities. If a company doesn’t respond or act quickly enough, the hacker may choose to disclose the info publicly even if the bug hasn’t been fixed.
Grey hats do this to gain popularity and recognition in the cyber security community, which indirectly helps them to grow their careers as security professionals. However, this step damages the reputation of the companies whose security vulnerabilities or exploits they disclose publicly.
For example, security researcher Anurag Sen and his team at Safety Detectives hunt for leaky databases and data breach incidents and draw the responsible officials’ attention before releasing such information in the public domain. They are responsible for exposing leaky databases of bigfooty.com, Avon, Natura & Co, RailYatri, and many others.
4) Red Hat Hacker
Much like white hat hackers, red hat hackers also want to save the world from evil hackers. But they choose extreme and sometimes illegal routes to achieve their goals.
Red hat hackers are like the pseudo-Robin Hood of the cybersecurity field — they take the wrong path to do the right thing. When they find a black hat hacker, they deploy dangerous cyber attacks against them.
Red hat hackers use all types of tactics to do this, including:
- Infecting the bad hackers’ systems with malware,
- Launching DDoS attacks,
- Using tools to gain remote access to the hacker’s computer to demolish it.
In short, red hats are the types of hackers who often choose to take aggressive steps to stop black hat hackers. They’re known to launch full-scale attacks to bring down the bad guys’ servers and destroy their resources.
5) Blue Hat Hacker
Two different definitions are prevailing within the cybersecurity field, and they have little to nothing in common. We’ll explore both of them now.
Blue Hat Hacker Definition 1: Revenge Seekers
These hackers don’t necessarily care about money or fame. They hack to take personal revenge for a real — or perceived — sleight from a person, employer, institution, or government. Blue hat hackers use malware and deploy various cyber attacks on their enemies’ servers/networks to cause harm to their data, websites, or devices.
Sometimes, blue hat hackers use various hacking technics to bypass authentication mechanisms to gain unauthorized access to their targets’ email clients or social media profiles. This gives them the ability to send emails and post inappropriate messages from those profiles to take revenge.
At times, they engage in doxxing and post personal and confidential data of their nemeses in public channels to ruin their reputations. Sometimes, ex-employees hack into companies’ servers or steal their customers’ confidential data and release it to the public just to damage their former employers’ reputations.
Blue Hat Hacker Definition 2: Outside Security Professionals
Blue hat hackers are security professionals that work outside of the organization. Companies often invite them to test the new software and find security vulnerabilities before releasing it. Sometimes, companies organize periodic conferences for blue hat hackers to find the bugs in their crucial online systems.
Blue hat hackers perform penetration testing and deploy various cyber attacks without causing damage. Microsoft often organizes such invite-only conferences to test its Windows programs. That’s why some blue hats are known as blue hat Microsoft hackers.
6) Green Hat Hacker
These are the “newbies” in the world of hacking. Green hat hackers are not aware of the security mechanism and the inner workings of the web, but they are keen learners and determined (and even desperate) to elevate their position in the hacker community. Although their intention is not necessarily to cause harm, they may do so while “playing” with various malware and attack techniques.
As a result, green hat hackers can also be harmful because they often are not aware of the consequences of their actions — or, worst, how to fix them.
Green Hat Hackers vs Script Kiddies
There’s another type of hacker that’s similar to a green hat hacker — they’re known as “script kiddies.” Script kiddies are also amateur hackers, but instead of learning new hacking techniques and programming, they’re simply interested in downloading or buying the malware, tools, and scripts online and use them. The main difference between green hats and script kiddie is that the former is quite serious and hardworking, having a clear vision to improve their skills. The latter, on the other hand, is just interested in using pre-existing scripts and codes to hack.
Green hat hackers often take the proper educational path, earning certificates, and taking skill development courses to learn hacking. But script kiddies simply find shortcuts, like watching YouTube videos or reading some online articles or forum discussions. Basically, they like to execute hacks and cyber attacks without having complete knowledge of the consequences.
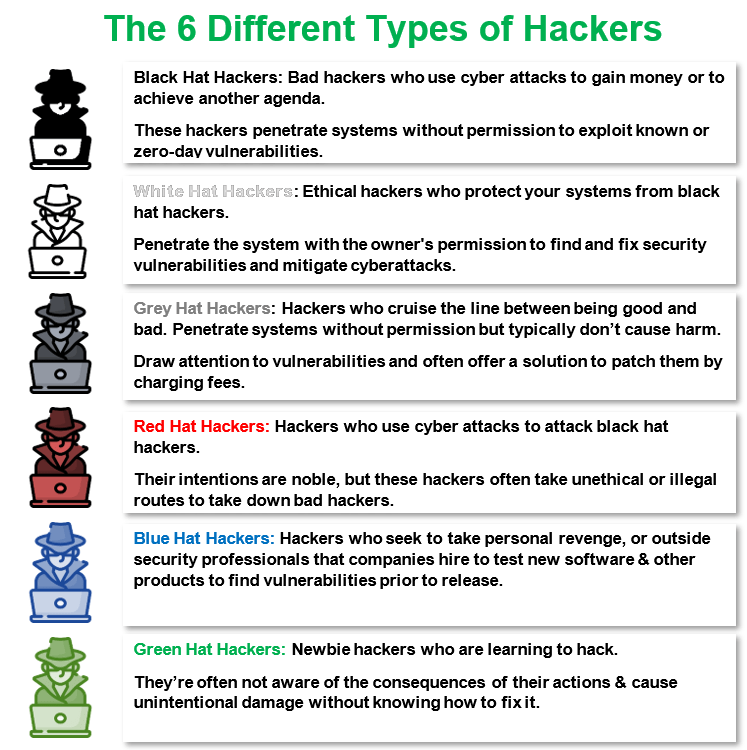
The 6 Different Types of Hackers
Don’t have a lot of time to read through each of the descriptions? No worries. We’ve got you covered in this quick recap:
Wrapping Up on the Different Types of Hackers
By now you must have a clear idea that not all hackers are the same. Sure, some hackers are bad guys (and gals) who use their technical skills to exploit other people and businesses. There is an interesting and in-depth interview of a black hat hacker named Irbis that highlights the motives, hacking tools, technics, risks, and financial rewards black hat hackers are getting. Here’s the article link: Black hat hacker interview. But there are also other types of hackers who are working day and night to protect us from those evil hackers. Some hackers even employ an aggressive approach and go up to any extent to destroy the notorious black hat hackers.
So now, when you hear the word “hacker” again, pause for a moment and ask yourself “which type of hacker?” instead of instantly imagining a bad guy in a hoodie!







![The TLS Handshake Explained [A Layman’s Guide]](https://sectigostore.com/blog/wp-content/uploads/2023/01/tls-handshake-feature-150x150.jpg)






 (72 votes, average: 4.76 out of 5)
(72 votes, average: 4.76 out of 5)






2018 Top 100 Ecommerce Retailers Benchmark Study
in Web Security5 Ridiculous (But Real) Reasons IoT Security is Critical
in IoTComodo CA is now Sectigo: FAQs
in SectigoStore8 Crucial Tips To Secure Your WordPress Website
in WordPress SecurityWhat is Always on SSL (AOSSL) and Why Do All Websites Need It?
in Encryption Web SecurityHow to Install SSL Certificates on WordPress: The Ultimate Migration Guide
in Encryption Web Security WordPress SecurityThe 7 Biggest Data Breaches of All Time
in Web SecurityHashing vs Encryption — The Big Players of the Cyber Security World
in EncryptionHow to Tell If a Website is Legit in 10 Easy Steps
in Web SecurityWhat Is OWASP? What Are the OWASP Top 10 Vulnerabilities?
in Web Security