- Home
- Security, Compliance, and Identity
- Microsoft Defender XDR Blog
- Microsoft Cloud App Security: The Hunt for Insider Risk
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Welcome back to our second post in the “Microsoft Cloud App Security: The hunt” series!
If you haven’t read the first post by Sebastien Molendijk, head over to Microsoft Cloud App Security: The hunt in a multi-stage incident - Microsoft Tech Community to see how you can leverage advanced hunting to investigate a multi-stage incident.
As stated previously, this series will be used to address the alerts and scenarios we have seen most frequently from customers and apply simple but effective queries that can be used in everyday investigations.
The below use case describes an avenue to diagnose that an insider is posing risk to an organization. One of the key things to understand about insider risk is that it is an investigation regarding inadvertent or intentional risks posed by employees or other members of the organization. It often requires the ability to understand the context of the user and also to quickly identify and manage risks. The methods we describe are one common way to get at the risk to an organization from an insider who is planning to exit the company.
Every step of this investigation should be done in coordination with your organization’s HR and Legal departments, adhering to appropriate privacy, security and compliance policies as set out by your organization. In addition, there may be training of analysts to handle this kind of investigation with specific and careful steps in accordance with your organization’s commitment to its employees.
Use case
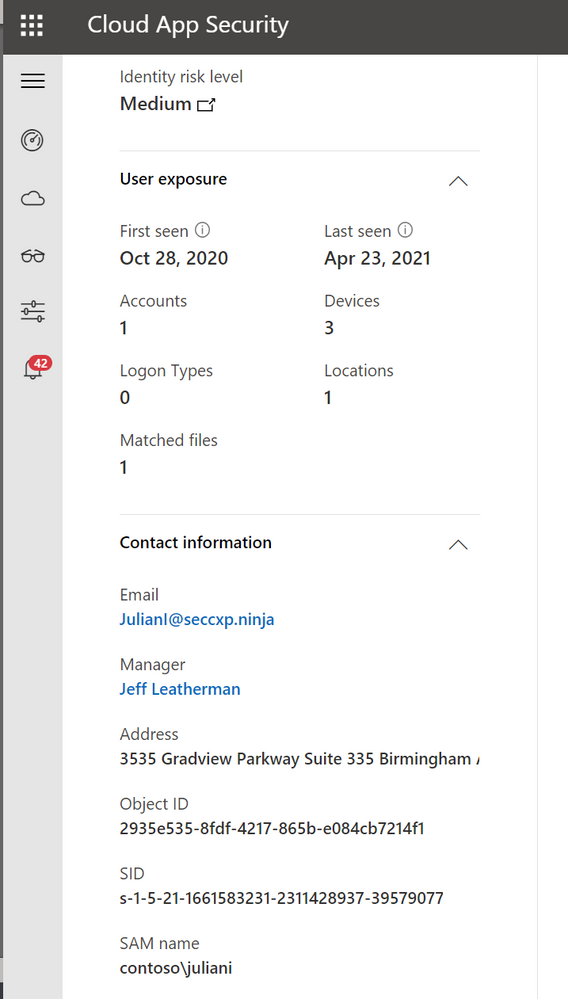
Contoso implemented Microsoft 365 Defender and is monitoring alerts using Microsoft’s security solutions. While reviewing the new alerts, our security analyst noticed a mass download alert that included a user named Julian Isla.
Julian is currently working on a highly confidential initiative called Project Hurricane. Knowing this, the analyst wants to conduct a thorough analysis in this investigation.
Our analyst can immediately see that Cloud App Security provides many key details in the alert, including the user, IP address, application and the location.
The first step for the analyst may be to gather details such as the device, the type of information downloaded, the user’s typical behavior and other possible activities that could mean data was exfiltrated.
Using the available details in the MCAS alert, and the initial questions and concerns of the investigation, we will showcase how to answer each step through an advanced hunting query and that the results of each query shape the follow-on query, allowing the investigator to piece together the full story from the activities logged.
|
Question 1: |
Query Used: |
|
What managed devices has this user logged in to?
|
|
NOTE: The analyst was able to extract the Security Account Manager (This can be done by using Cloud App Security’s entity page.
NOTE: If the analyst wanted to display the entire LoggedOnUsers table, the column would look like this:
[{"UserName":"JulianI","DomainName":"CONTOSO","Sid":"S-1-5-21-1661583231-2311428937-3957907789-1103"}]
Result:
Using this query that surfaces Microsoft Defender for Endpoint (MDE) data, the analyst found that Julian used two devices today, adminpc.contoso.azure and victimpc.contoso.azure. More importantly, the analyst can see that Julian was on the adminpc device on the same day as the alert for a mass download was triggered.
|
Question 2: |
Query Used: |
|
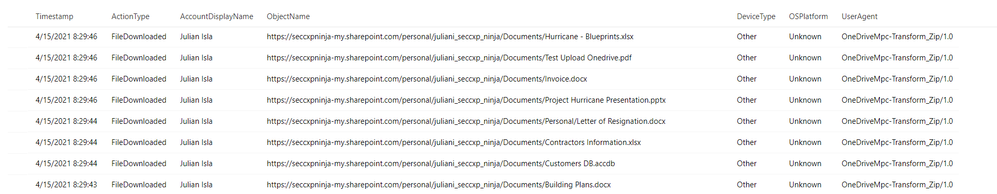
Were the files downloaded to a non-managed device?
|
|
Result:
By using the CloudAppEvents table, the analyst can now view the file names and the number of files and devices Julian used to complete these downloads. They can determine by the names of the files and the device details that Julian has downloaded important proprietary company data for Project Hurricane, a high-profile initiative for a new application that includes sensitive customer data and source code.
|
Question 3: |
Query Used: |
|
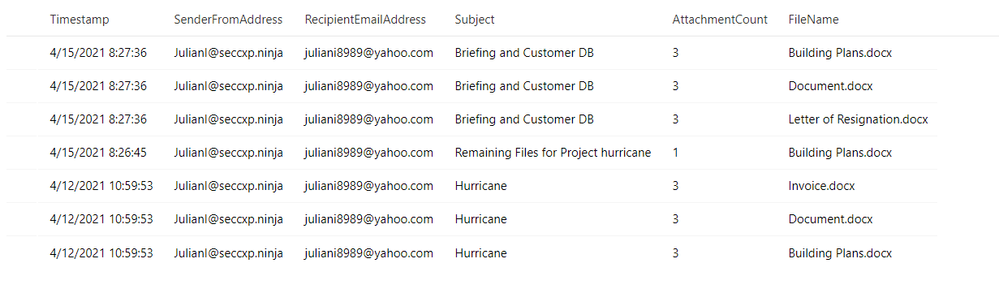
Has this user leveraged personal email in the past?
|
|
Result:
|
Question 4: |
Query Used: |
|
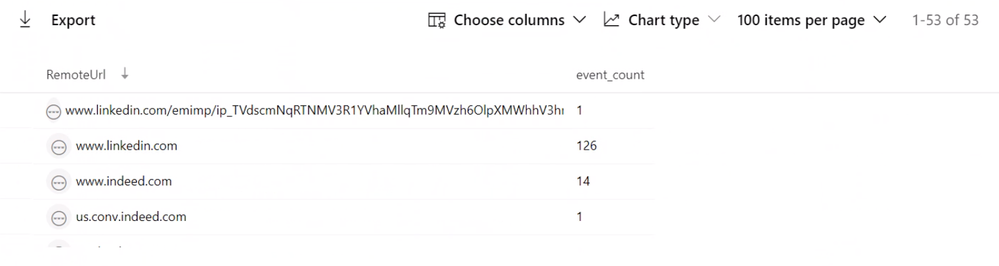
Has this user been actively job searching?
|
|
Result:
While investigating the DeviceNetworkEvents table to find if this user may have motivation to be conducting these types of activities, they can see this user is actively surfing job sites and may have plans to leave their current role at Contoso.
|
Question 5: |
Query Used: |
|
Does this user have a Letter of Resignation or Resume Saved to their local PC?
Does this user have a Letter of Resignation or Resume Saved to their personal OneDrive?
|
|
Result:
The analyst is attempting to establish the user’s planned trajectory of actions and sees that they currently have a letter of resignation saved to their desktop and have recently accessed and downloaded it.
|
Question 6: |
Query Used: |
|
Have any removeable media or external devices been used on the PCs we discovered?
|
|
Result:
Luckily, the analyst can determine that files were not exfiltrated because there is no record of a removable media device data transfer from the user’s most recently used device.
Throughout the investigation, the analyst had many avenues to pursue and potential ways to mitigate and prevent further exfiltration of data. For example, using Cloud App Security’s user resolutions, the analyst could have suspended the user. Additionally, using Microsoft Defender for Endpoint integration, the analyst could have isolated the managed device, preventing it from having any non-related network communication.
In conclusion, in this test scenario, the Contoso employee, “Julian” had been violating company policy and exfiltrating proprietary data for Project Hurricane to his personal laptop and email account for some time. They also found that the user had been actively job searching and had a recently edited version of a letter of resignation saved to t. Using the initial MCAS alert, as well as logs across Microsoft Defender for Endpoint and Microsoft Defender for Office 365, the analysts have discovered and prevented further data loss for the company by this user.
This completes our second blog, please stay tuned for other common use cases that can be easily and thoroughly investigated with Microsoft Cloud App Security and Microsoft 365 Defender!
Resources:
For more information about the features discussed in this article, please read:
- Advanced hunting overview
- Advanced hunting best practices
- Cloud App Security anomaly detection alerts investigation guide
- Microsoft 365 Defender Github
Feedback
We welcome your feedback or relevant use cases and requirements for this pillar of Cloud App Security by emailing CASFeedback@microsoft.com and mention the area or pillar in Cloud App Security you wish to discuss.
Learn more
For further information on how your organization can benefit from Microsoft Cloud App Security, connect with us at the links below:
|
Join the conversation on Tech Community. Stay up to date—subscribe to our blog. |
Upload a log file from your network firewall or enable logging via Microsoft Defender for Endpoint to discover Shadow IT in your network. |
|
Learn more—download Top 20 use cases for CASB. |
Connect your cloud apps to detect suspicious user activity and exposed sensitive data. |
|
Search documentation on Microsoft Cloud App Security. |
Enable out-of-the-box anomaly detection policies and start detecting cloud threats in your environment. |
|
Understand your licensing options. |
Continue with more advanced use cases across information protection, compliance, and more. |
|
Follow the Microsoft Cloud App Security Ninja blog and learn about Ninja Training. Read up on recent blogs: aka.ms/MCASMarch2021 Go deeper with these interactive guides: · Discover and manage cloud app usage with Microsoft Cloud App Security · Protect and control information with Microsoft Cloud App Security · Detect threats and manage alerts with Microsoft Cloud App Security · Automate alerts management with Microsoft Power Automate and Cloud App Security |
|
Follow us on LinkedIn as #CloudAppSecurity. To learn more about Microsoft Security solutions visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity on Twitter, and Microsoft Security on LinkedIn for the latest news and updates on cybersecurity.
Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.