- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- DevOps Security Workbook
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
DevOps Security Workbook
Workbooks provide a flexible, customizable canvas for data analysis and the creation of rich visual reports. The new DevOps Security workbook in Microsoft Defender for Cloud (MDC) provides you with a unified interactive experience enabling you to quickly gain visibility and insights into your DevOps security posture in coordination with the newest MDC service Defender for DevOps. The DevOps Security workbook provides you with a customizable foundation that helps you visualize the state of your DevOps posture for the connectors you have configured. You can investigate credential exposure, including types of credentials and repo locations. Then you can do the same for code, dependencies, and hardening.
Objectives: Create a centralized view of DevOps security to inform investigations and enable reporting capabilities for your organization
- Overview - summary view of code, secrets, OSS vulnerabilities, and posture scan results
- Secrets - view of exposed secrets in repositories
- Code - view of code scanning results in repositories
- OSS Vulnerabilities - view of OSS vulnerabilities in repositories
- Infrastructure as Code - view of IaC misconfigurations in repositories
- Posture - consolidated view of security posture across connected DevOps environments
- Threats & Tactics - summarized view of attack exposure across connected DevOps environments
Prerequisite:
- To leverage the DevOps Security Workbook you must have a connector provisioned in MDC to your Source Code Management System (such as Azure DevOps or GitHub)
Access the Workbook
- Navigate to Defender for Cloud, click on Workbooks, then click on DevOps Security (Preview) to launch the Workbook.
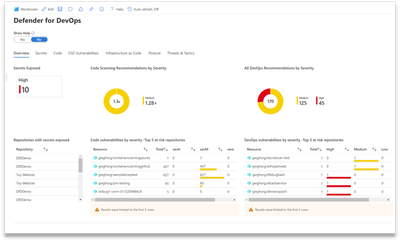
Overview Page
The Overview page is the aggregated information for the DevOps Security Workbook. The Help button shows a description for each tab and links to each DevOps Recommendation in Defender for Cloud.
The Overview graphs show overall secrets exposure, cumulative code scanning findings, and all DevOps Recommendations by severity. The top repositories requiring attention, ordered by discovered security issues, are listed below each graph.
Secrets Page
The Secrets page shows the repositories and the exact location—down to the line of code—where a secret has been found in a source file. Data also includes the type of secrets found across repositories. This enables Security Operators to know what types of secrets are commonly exposed in your organization and where to go to immediately disable compromised secrets in cloud resources and workloads.
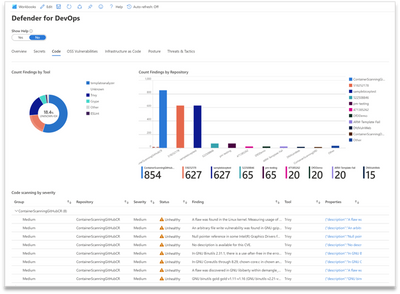
Code Page
The Code page shows code scanning findings aggregated by tool (such as TemplateAnalyzer, Trivy, etc.) and by repository. The threshold is set to 10 but can be changed to match your organization’s tolerable risk level for code security issues. You’ll know which repositories have a high number of security findings so that Security Operators can focus efforts with those Development Teams needing security awareness training.
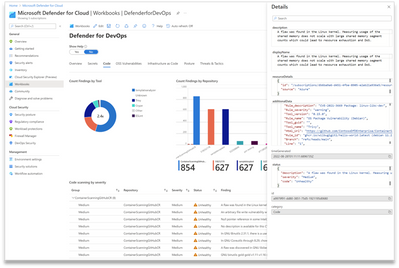
Additional information available in the Properties column includes details on the analysis performed and data collected during code scanning including description, deep link to the file with the security issue, tools, rules, branches, line number, severity, and more. You can use this rich data to further customize the Workbook’s analysis for your organization’s needs using Kusto Query Language (KQL).
OSS Vulnerabilities Page
The OSS Vulnerabilities page shows vulnerable open source dependencies used in a workload. Results are grouped by repository in the grid view and, again, you can drill down in the Properties column to see supplementary information such as CVE, CWE, CVSS score, and more. This data is useful for focusing remediation efforts on specific vulnerable repositories and workloads.
Infrastructure as Code Page
The Infrastructure as Code page contains IaC misconfiguration findings by tool and by repository. This data is useful for proactively identifying repositories with misconfigured IaC templates that could lead to deploying vulnerable workloads.
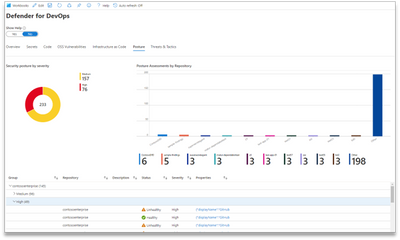
Posture Page
The Posture page consolidates the view of security posture of DevOps repositories. The issues surfaced on this page are related to good code hygiene practices and security configuration of DevOps environments. Some examples include seeing whether code, secret, and OSS vulnerability scanning is enabled on a repository.
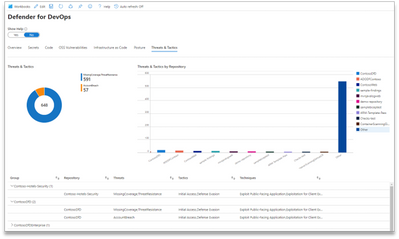
Threats & Tactics Page
This page is a view of repositories and all their issues with the corresponding threats and tactics that could be used to exploit the discovered vulnerabilities. Security Operators can use this date to proactively work with Development Teams to reduce attack surface. This data also allows your Threat Hunters to prioritize hunting and response based on the types of attacks that are high priority to your organization.
Conclusion
To review, we’ve walked through the new DevOps Security Workbook and explored how you can gain new visibility into the security posture of your Source Code Management Systems (SCMS) in Microsoft Defender for Cloud. Once you’ve onboarded your SCMS—whether GitHub, Azure DevOps, or even future integrations—to Defender for DevOps, you can visualize the security of your development lifecycle across any cloud—Azure, AWS, GCP—and build rich, customized dashboard experiences with KQL to enable the centralized view of DevOps Security that empowers and informs your organization.
Additional Resources
- To learn more about Defender for DevOps, read this documentation
- Download (free) a special Appendix about Defender for DevOps from the latest Microsoft Defender for Cloud book published by Microsoft Press
- To learn how to onboard your Source Code Management System to Defender for Cloud, read this documentation for GitHub and this documentation for Azure DevOps
- To learn more about the Microsoft Security DevOps (MSDO) tools, read this documentation for GitHub and this documentation for Azure DevOps
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.