- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Pre-Deployment Protection for Infrastructure as Code
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Pre-Deployment Protection for Infrastructure as Code
Security Operators are inundated with security misconfigurations in their cloud resources. To reduce the number of security misconfigurations, identification and remediation can be shifted left so Developers can find and fix security misconfigurations earlier in the development lifecycle, reducing the burden on SecOps. Let's see how the newest service in Microsoft Defender for Cloud, Defender for DevOps, can help with pre-deployment protections. This blog walks Security Operators through setting up security tools in development workflows and integrated developer environments (IDE)—enabling SecOps to empower their Developers to fix security misconfigurations in pre-deployment, before the issues are deployed to production.
Objectives:
- Configure the Defender for DevOps Microsoft Security DevOps (MSDO) tools to scan for Infrastructure as Code (IaC) templates
- Leverage GitHub branch protection to require Checks for TemplateAnalyzer and Terrascan rules
- Use a GitHub extension to manage pull requests and visualize Checks from the MSDO tools and indicate the exact lines of code that are misconfigured
Prerequisites:
- Connector provisioned in MDC to your Source Code Management System (such as Azure DevOps or GitHub)
- If your SCMS is GitHub: GitHub Advanced Security
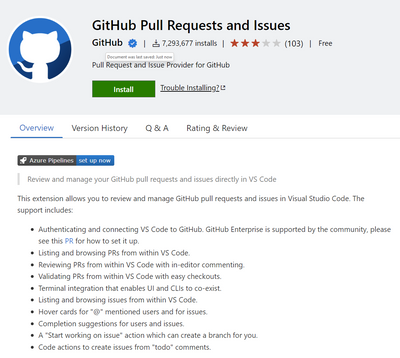
VS Code GitHub Extension
The GitHub Pull Requests and Issues extension allows you to review and manage GitHub pull requests and issues in Visual Studio Code. It allows you to manage pull requests and finds issues with checks annotated in IaC templates. The extension can be found at this link: https://marketplace.visualstudio.com/items?itemName=GitHub.vscode-pull-request-github
Defender for DevOps IaC Tools
The Microsoft Security DevOps (MSDO) tools are a set of static code analysis tools that help you secure workloads in your CI/CD pipelines. The tool configuration supports enabling only Infrastructure as Code, without the other tools, to shorten runtime and concentrate on securing ARM, Cloud Formation, Terraform templates.
- Configure the MSDO tools for only IaC scanning, follow the tutorial at this link: https://docs.microsoft.com/en-us/azure/defender-for-cloud/iac-vulnerabilities
GitHub Branch Protection Rule
This section assumes you followed the steps in the previous section to configure the MSDO tools.
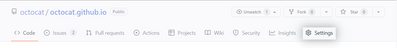
Next, navigate to the repository you used to setup the MSDO tools.
1. On GitHub.com, navigate to the main page of the repository
2. Under your repository name, click Settings
3. In the "Code and automation" section of the sidebar, click Branches
4. Next to "Branch protection rules," click Add rule
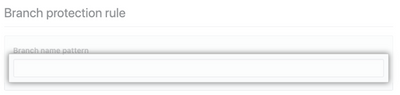
5. Under "Branch name pattern," type the branch name or pattern you want to protect
If you want to support all branches, type * or enter your default branch name
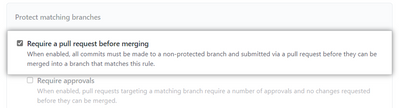
6. Under "Protect matching branches," select Require a pull request before merging
7. Select Require status checks to pass before merging
8. In the Search for status checks box, type Terrascan and TemplateAnalyzer
9. Optional: select Include administrators to apply the rules above to administrators
10. Click Save
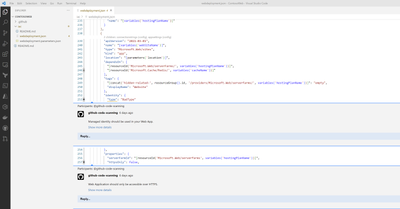
Upload and Test an ARM Template
11. In the IaC tutorial, you downloaded an ARM template to get started
Make a change to the template and commit it to a new branch
12. Create a pull request
13. Check the pull request results of the MSDO workflow
14. Verify that Checks show up in VS Code
Conclusion
To review, we’ve walked through creating a branch protection rule to force the Infrastructure as Code MSDO tools to run when a pull request is submitted. The tools found misconfigurations in templates and did not allow the pull request to merge into the main branch because of the security findings in the templates. This not only helps reduce the fatigue of Security Operators, but also empowers Developers to find and fix security misconfigurations before they ship to production.
Additional Resources
- To learn more about Defender for DevOps, read this documentation
- Download (free) a special Appendix about Defender for DevOps from the latest Microsoft Defender for Cloud book published by Microsoft Press
- To learn how to onboard your Source Code Management System to Defender for Cloud, read this documentation for GitHub and this documentation for Azure DevOps
- To learn more about the Microsoft Security DevOps (MSDO) tools, read this documentation for GitHub and this documentation for Azure DevOps
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.