- Home
- Public Sector
- Public Sector Blog
- Microsoft Teams in Office 365 GCC High - CMMC Considerations
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Department of Defense (DoD), its agencies and organizations, and supply chain - Defense Industrial Base (DIB) - have shied away from remote working and SaaS offerings in the cloud for understandable security concerns. However, times have changed. The workforce includes several new generational bands, technology has inhibited new possibilities, and cybersecurity products/tools are far more enhanced than 10 years previously.
Additionally, threats to operational continuity like the recent COVID-19 pandemic are becoming an almost annual occurrence. Weather events, physical security threats, power outages, cyber attacks, and other external factors create scenarios where working from home or remotely becomes the best option for a group of users (if not the entire enterprise). Enter Microsoft Teams for Microsoft 365 GCC High.
Below is a quick video if you've never demo'd Teams or seen the SaaS communication and collaboration suite in action.
A Forrester study conducted in 2019 provided several encouraging findings about Microsoft Teams :
-
4hours/week estimated time saved by information workers through improved collaboration and information sharing
-
17.7% improvement of time-to-decision made by decision makers
-
18.9% reduction in meetings each week
Collaboration with Teams in Microsoft 365 GCC High
Regardless of your corporate policies, device makeup, approved browsers, and varying governance factors - your users can access Microsoft Teams from almost every major end point.
Unlike Microsoft technologies before it, Teams is not limited to specifically chat/meetings/calling (like with Skype of old) or document management/collaboration (as with SharePoint). Government contractors are adopting this primarily because of its centralized functionality. IT Managers and CIO's alike enjoy training employees on a single tool or software rather than many.
Teams allows a user to create, store, share, and collaborate on files without leaving the application (or their kitchen table). In the Forrester study mentioned above, 88% of users surveyed noted “having all of our solutions in one place saves time”: Additionally, users can access native Office productivity tools like Excel, PowerPoint, and Word without the need to open up the local desktop application.
Security and Compliance with Teams in Microsoft 365 GCC High (M365)
Microsoft Teams in Microsoft’s sovereign environments for US Government can meet many of the requirements in CMMC pertaining to information systems in the cloud. Much of which is met through overarching Office 365 security and products. For starters, the Identification and Authentication (IA) requirements (1.077, 2.078, 2.079, 2.080, 2.081, 2.082, 3.083, 3.084) are met in spades by properly configured Azure Active Directory and Multi Factor Authentication (MFA) within the Office 365 GCC High tenant. This of course extends to Microsoft Teams, as well as SharePoint and others.
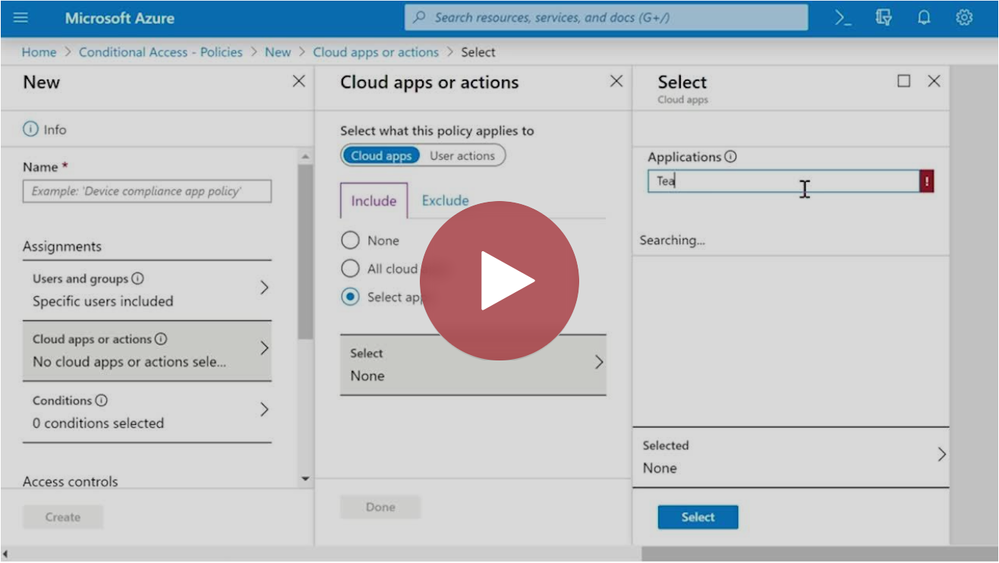
According to the Media Protection (MP) domain, 2.120 and 3.124 DoD suppliers are responsible for limiting "access to CUI on system media to authorized users" and "control access to media containing CUI and maintain accountability for media during transport outside of controlled areas." Many companies previously feared the move away from VPNs and Virtual Desktops towards cloud SaaS and PaaS solutions because of the perceived lack of control and ability to meet the above compliance requirements. Conditional Access policies and others can be configured for Microsoft Teams to gain the necessary level of control.
As the visual below demonstrates, an administrator can block access to Teams during the authentication process before a user (or bad actor) can reach the application or data. The denial of access can be set based upon the device (managed or unmanaged), where the authentication attempt is coming from, and more.
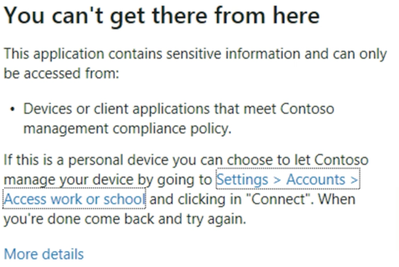
The end result for the user is a message that looks like the following. This prompt also includes a link to enroll the device into Intune, which is an additional governance and compliance benefit for users (not threats). As any IT leader knows, sometimes users do not read the first or fifth email about IT/security instructions.
On the topic of Intune, administrators can establish Intune Mobile Application Management (MAM) policies to block individuals from sharing files or copying and pasting content from Microsoft Teams to other applications like Gmail, the native Apple Mail on iOS devices, or a personal storage application (Dropbox, Box, etc.). Access Control (AC) 2.016 also states businesses need to "control the flow of CUI in accordance with approved authorization" Intune helps determine how Teams and the data residing within can interact with other functions and services locally installed on each end point within your environment.
Another Data Security measure is the use of Data Loss Prevention (DLP) to block sensitive transmissions containing CUI or other company proprietary data. DLP policies can be configured to prevent sharing sensitive text, as shown in the clip below, or documents through retention labels. DLP can also prompt users when a document or file is suspected of containing sensitive information to apply a label before sending.
The combination of Conditional Access, Intune, and DLP also address large portions of the System and Communications Protection (SC) requirements in CMMC. SC.1.175 requires the DIB to "monitor, control, and protect organizational communications at the external and internal boundaries of information systems." The external boundary of Office 365 GCC High at the network layer is handled by Microsoft and their own Firewalls and Web Proxies; however, the internal boundary for Microsoft Teams is controlled and protected by the aforementioned products. Microsoft Teams data is also encrypted in transit and at rest to meet SC.3.177.
Lastly, eDiscovery within Office 365 GCC High allows investigation of complete feeds as a relatively new feature. No longer can insider threat dialogue or traffic associated with an incident be buried within chat feeds. eDiscovery allows an administrator to search for traffic around a term, phrase, or string of characters and numbers in Microsoft Teams across every user. This assists in meeting some of the social aspects of Incident Response (IR), specifically 2.097 "Perform root cause analysis on incidents to determine underlying causes."
Limitations with Office 365 GCC High
Recently Audio Conferencing for Teams (Direct Routing) and Phone System for Teams (Direct Routing) became generally available. Unlike the commercial Office 365 and Teams offering where Microsoft provides phone numbers and calling plans, DoD suppliers must create their direct inward dial through Direct Routing. This allows employees to call out to a phone number (non-Teams resource) from a phone system and an external phone call can be delivered directly to a phone number associated with a user in Teams. This also allows for Teams Dial-in conference numbers. For more information on an audio conferencing solution in Office 365 GCC High click here.
You also do not presently have the ability to externally share with other organizations via Teams or provide guest access; however, GCC High to GCC High (B2B) sharing should be available this year. Also, meeting/call recording is currently unavailable.
As Users Control More - So Do Administrators
Security and compliance do not take a backseat in the midst of enhanced mobility and cloud adoption. The below diagram (created by Microsoft) articulates the level of control admins have over their company's content, collaboration, and communication.
For more on Data Loss Prevention and Data Labeling, check out this five minute snapshot from the Cloud Security and Compliance Series (CS2) event in Indianapolis, Ben Curry - Principal Architect at Summit 7 discussed the importance of labeling CUI for CMMC compliance and proper data protection.
About the Author
Ben Curry
Ben Curry, CISSP is a business leader, author, and enterprise architect specializing in the Microsoft Sovereign Cloud and Enterprise Mobility + Security. Ben is a Managing Partner at Summit 7 Systems, a Microsoft Gold Partner helping Aerospace and Defense companies build and manage cloud environments for operational, security and compliance requirements. Ben is honored to have received 11- Microsoft Most Valuable Professional (MVP) awards due to his investments in, both, the SharePoint and Office 365 community – along with championing transformational projects for several non-profits. He is a former NASA Data Center Lead and Architect, and has several published works through Microsoft Press - most recently "From IT Pro to Cloud Pro Microsoft Office 365 and SharePoint Online
Original Posting: Microsoft Teams in Office 365 GCC High - CMMC Considerations
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.