- Home
- Azure
- Azure Virtual Desktop
- Step by step guide on computer account auth for Azure Files
Step by step guide on computer account auth for Azure Files
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 04 2020 02:58 PM - edited Nov 04 2020 06:49 PM
Step by step guide on computer account auth for Azure Files
In the last 3 weeks, I have been getting a lot of questions around Azure Files. The main question has been “Can computer accounts have access Azure Files?”. This combined with my work on MSIX app attach (which also uses Azure Files) has prompted the creation of this post.
Prerequisites
Azure Files supports multiple authentication mechanisms. This article is focused on authenticating with
AD DS, as described here. Hence the prerequisites are:
- AD DS synched to Azure AD
- Permissions to create a Group in AD DS
- Storage account or enough permissions to create one
- VM or physical machine joined to AD DS, and permissions to access it
- WVD host pool in which all session hosts have been domain joined
Process overview
1. Create AD DS security group.
2. Add the computer accounts for all session hosts as members of the group
3. Synch AD DS group to Azure AD
4. Create storage account
5. Create file share under the storage account
6. Join storage account to AD DS
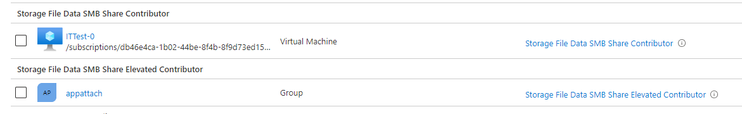
7. Assign the AD DS group that has been synched to Azure AD, the Storage File Data SMB Share Contributor role assignment on the storage account
8. Mount file share on any session host
9. Grant NTFS permissions on the file share to the AD DS group
Create Group in AD DS
This group will be used in later steps to grant share level and (files share) permissions.
- Remote into the VM or physical machine joined to AD DS.
- Open the Active Directory Users and Computers utility.
- Under the domain node right click and select New, and then Group.
Note: it is not mandatory to create a new group, an existing group can be used.
- In the New Object – Group enter group name and select:
- Group scope: Global
- Group type: Security
- Right click on the new group and select Properties.
- In the properties screen select the Members tab.
- Click Add…
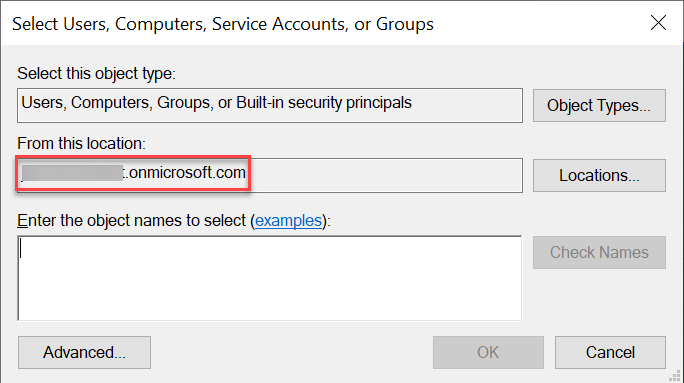
- In the Select Users, Contacts, Computers, Service Accounts, or Groups dialog click Object Types… and select Computers. Click OK.
- In the Enter the object names to select enter the names of all session hosts.
- Click Check Names and if multiple entries are present select the “correct” one from the results dialog.
- Press Ok and then Apply.
Note: If this is a new group it may take up to 1 hour to sync with Azure AD.
Create storage account
For brevity we will assume there is already a storage account with a file share. If required, please reference this article on how to create storage accounts. If you’re creating a new storage account, it is mandatory to create a file share.
Note: if you are creating a Premium storage account make sure Account Kind is set to FileStorage.
Share-level permission aka RBAC permission
- Select the desired storage account
- Click Access Control (IAM) and then Add. From the drop down select Add role assignments.
- In the Add role assignment screen:
- Role: Storage File Data SMB Share Contributor
- Assign access to: User, Group, or Service Principal
- Subscription: Based on your environment
- Select: pick the AD group that you created which contains your session hosts
- Click Save
Join storage account to AD DS
In this step we are going to join our storage account to AD DS. The full article is available here. Please note our steps here have been modified to achieve the desired scenario.
- Remote into the VM or physical machine joined to AD DS
Note: Run the script using an on-premises AD DS credential that is synced to your Azure AD. The on-premises AD DS credential must have either the storage account owner or the contributor Azure role permissions.
- Download and unzip the latest version on AzFilesHybrid from here.
- Open PowerShell in elevated mode.
- Run the following command to set the execution policy:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope CurrentUser - Navigate to where AzfileHybrid was unzipped and run .\CopyToPSPath.ps1
- Import the AzFilesHybrid module via Import-Module -Name AzFilesHybrid
- Connect to Azure AD via Connect-AzAccount
- Set the following parameters according to your setup:
$SubscriptionId = "<your-subscription-id-here>" $ResourceGroupName = "<resource-group-name-here>" $StorageAccountName = "<storage-account-name-here>"
- Run Join-AzStorageAccountForAuth
Join-AzStorageAccountForAuth ` -ResourceGroupName $ResourceGroupName ` -StorageAccountName $StorageAccountName ` -DomainAccountType "ComputerAccount" ` -OrganizationalUnitDistinguishedName "<ou-here>" ` -EncryptionType "'RC4','AES256'"
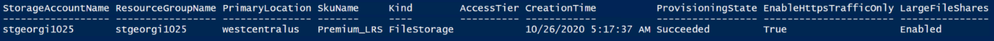
- The output of the above command must look like the screenshot below. If it doesn’t, joining the storage account to AD DS was not successful.
File-level permissions aka NTFS permissions
To be able to authenticate with AD DS computer accounts against an Azure Files storage account, we must also assign NTFS level permission in addition to the RBAC permission we set up earlier.
- Open the Azure portal and navigate to the storage account that we added to AD DS.
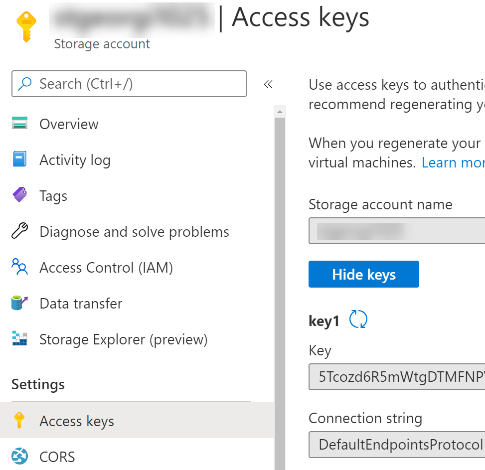
- Select Access keys and copy Key1
- Remote into the VM or physical machine joined to AD DS.
- Open command prompt in elevated mode.
- Execute the following command replacing the values in it with those applicable to your environment:
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> /user:Azure\<storage-account-name> <storage-account-key>
Note: Make sure that the output of the command above is “The command completed successfully”.
If not, repeat and verify input.
- Open File Explorer and find the drive letter specified in the command above.
- Right click on the drive letter and select Properties and then Security.
- Click Edit and after that Add…
Note: Make sure that domain name matches your AD DS domain name, if it doesn’t the storage account has not been domain joined.
- If prompted, enter admin credentials.
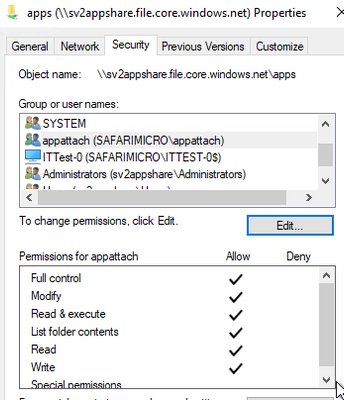
- In the Select Users, Computers, Service Accounts, or Groups window enter the name of the group we created in the Create Group in AD DS section
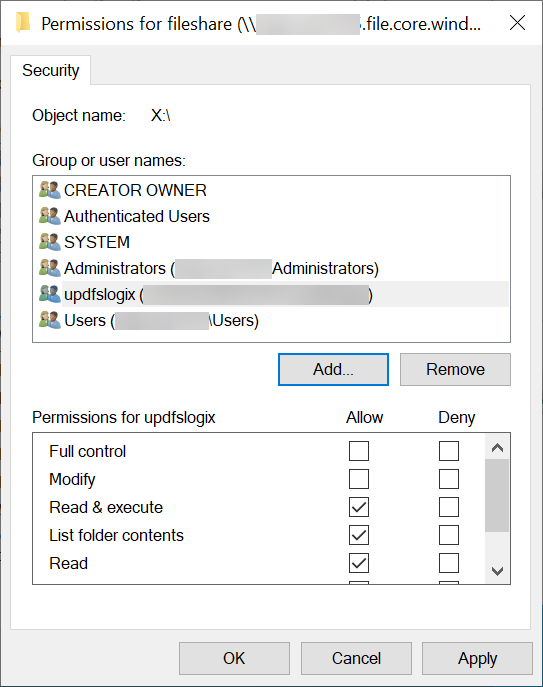
- Click OK and confirm the group has Read & execute permissions.
- Add the AD group with the computer accounts with Read & execute permissions.
- Click Apply and if prompted by Windows Security confirm by pressing Yes.
Troubleshooting
Common challenges with granting machine accounts access to Azure Files share authenticated with Azure AD are captured in the sections below.
Group membership
When a VM is added to an AD DS group that VM needs to be restarted in order to pick up its membership to the group.
Adding storage account to AD DS
The Azure Files team have excellent troubleshooting document available here. There are few errors that I have observed occurring with higher frequency:
- Ignoring warnings when running the PowerShell This will cause the account to be created but possibly with certain incorrect setting. This is where it is easier to delete the domain account representing the storage account and try again.
- Incorrect OU specified It is a best practice to specify an OU for your storage account. The way an OU is specified is using the standard syntax (DC=ouname,DC=domainprefix,DC=topleveldomain – for example DC=storageAccounts,DC=wvdcontoso,DC=com)
- Storage account synch to Azure AD It will take about 30 minutes for the storage account to synch to Azure AD.
Synching AD DS group to Azure AD
The synch interval between AD DS and Azure AD is 30 minutes by default. If the AD DS group was create in the last 30 minutes and cannot be assigned to the storage account, option 1 is to wait, option 2 is to force the AD DS -> Azure AD sync. Sample script, here.
RBAC permissions
For MSIX app attach and FSLogix the minimum RBAC permissions on the storage account are Storage File Data SMB Share Contributor.
NTFS permission
For MSIX app attach and FSLogix the minimum NTFS permissions on the storage account are Read & Execute, and List folder content.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 05 2020 08:15 AM
Great article @Stefan Georgiev
Anyone interested in seeing a video walking through this process check out The Azure Academy
video on Azure Files with AD Authentication
https://www.youtube.com/watch?v=9S5A1IJqfOQ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 05 2020 08:17 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 29 2021 02:30 PM
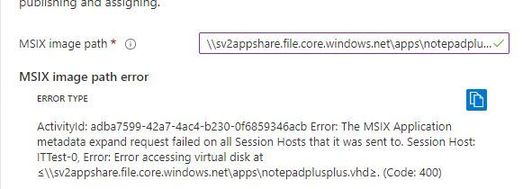
Have you gotten app attach to work on on azure file share with Azure ADDS? Despite having Azure AD DS enabled on the storage, and the session host's managed identity added to the file share SMB share contributor role and able to mount the file share successfully from the session host and have assign full access in the NTFS permissions for the the session host's account and users, getting an 'Error accessing virtual disk' when trying to enter the msix image path (see screenshot below). Any ideas?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 29 2021 02:40 PM
As to the specific question on AADDS being compatible/supported with the portal MSIX AppAttach feature...I’ll let Stefan give the official response ☺️
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 29 2021 04:54 PM
Thanks Dean - found a response from Stefan and Tom Hickling on another forum post from earlier this month so I'm guessing its still not a workable scenario at this point.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 07 2021 08:09 AM
@JeremyWallace I tried the SAS key approach and can't get that to work either. It would be nice if Stefan could give us actual steps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 08 2021 07:35 AM
@mobilejon thanks for the suggestion. We will consider it. Two things to keep in mind we are working on something that may render the need for Azure AD DS obsolete and Azure AD DS has a very low adoption in enterprise (last time I checked less than 3%)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 08 2021 07:39 AM
@Stefan Georgiev for our organization, the need for LDAP translation from cloud-only accounts is very important.
Do you have steps to actually make this work in AAD-DS that have been tested and actually work?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 08 2021 12:25 PM
@JeremyWallace , were you able to find a solution for this issue? We have same setup. Cloud only users and AADDS. Can't get MSIX app attach to work. Have you tried a file share on an Azure VM? Not sure what other options there might be. Just looking for ideas. Amazing how hard it's been to find info on this. Usually they will tell you that Hybrid Auth is REQUIRED or something like that but they don't in the documentation. Pretty frustrating. Thanks for any ideas.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 08 2021 01:14 PM
@Chrisvanaz I don't believe that MSIX App Attach is supported with Azure AD Domain Services at all today.
I believe part of this limitation is that you don't have any rights in the AADDS Domain to assign NTFS permissions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 08 2021 01:27 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 22 2021 10:57 AM
@Dean Cefola you are correct, we are adding this disclaimer to our documentation